Trezor Login: The Ultimate Gateway to Secure Crypto Management
In the fast-paced and often risky world of cryptocurrencies, securing your digital assets is a top priority. With the rising number of scams, phishing attacks, and hacking attempts, users need a login system that is both strong and reliable. Trezor Login, created by SatoshiLabs, provides one of the most secure methods for accessing and managing your cryptocurrency holdings. It replaces traditional password systems with hardware-based authentication, giving users complete control and peace of mind.
What Is Trezor Login?
Trezor Login is the secure process used to access your cryptocurrency wallet through a Trezor hardware wallet. Instead of relying on passwords or centralized systems that can be hacked, Trezor Login uses physical verification through your Trezor device. This ensures that only you — the device owner — can access your wallet and authorize transactions.
When you log in to your wallet using Trezor, your private keys remain safely stored within the hardware wallet itself. They never leave the device or appear online, even during login or transaction approval. This separation from the internet is what makes Trezor Login far safer than any software-based wallet or exchange account.
How Trezor Login Works
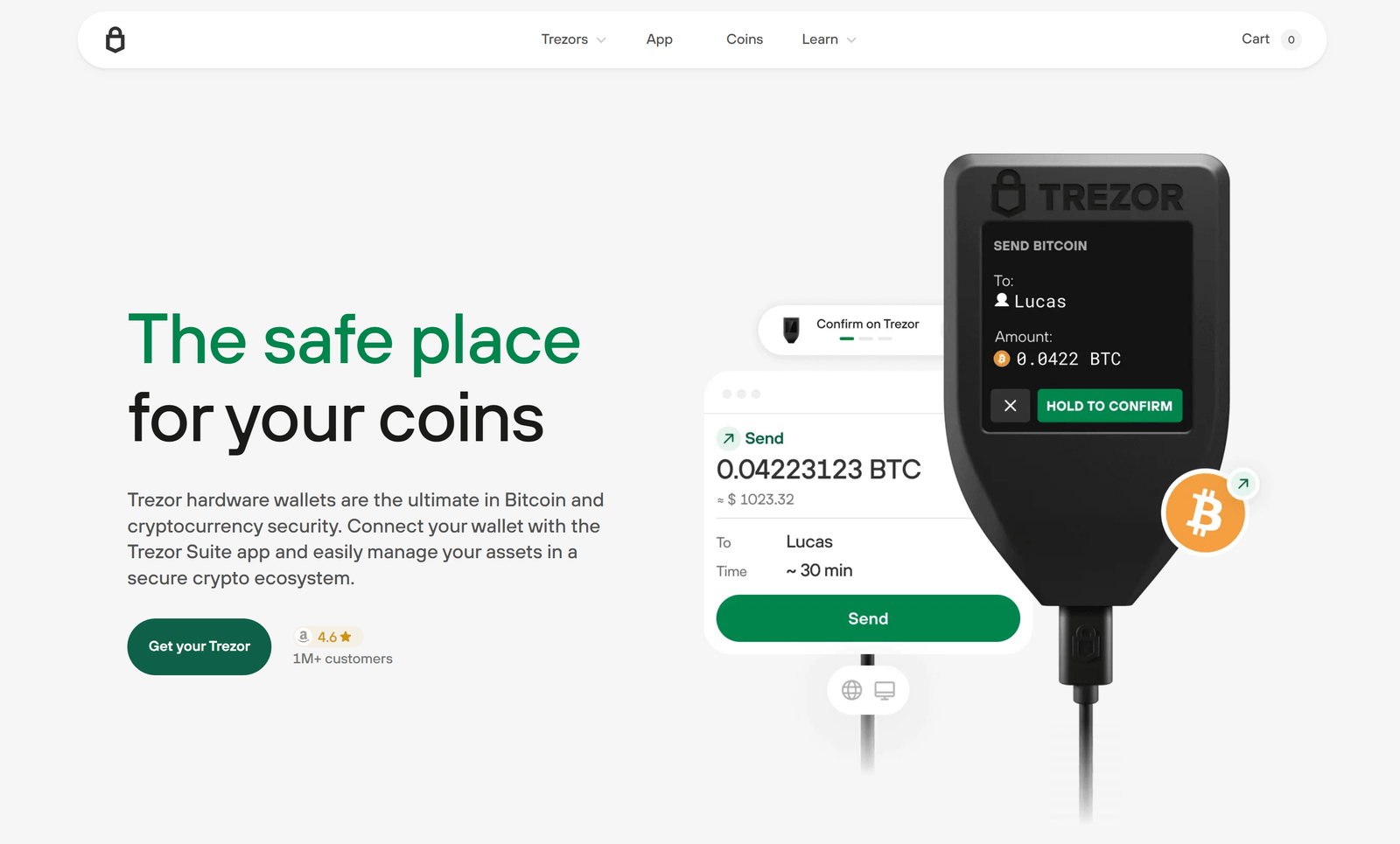
The Trezor Login process is simple and intuitive, designed to provide maximum security with minimal effort. When you connect your Trezor hardware wallet — such as the Trezor One or Trezor Model T — to your computer, the Trezor Suite application automatically detects the device.
You are then prompted to enter your PIN on the device, using a unique layout that changes each time you log in. This makes it impossible for keyloggers or malicious software to capture your PIN. If you have added an optional passphrase, you can enter that as well for an additional layer of security. Once verified, you gain instant access to your crypto dashboard through Trezor Suite, where you can view balances, manage transactions, and explore your portfolio — all while keeping your private keys securely offline.
Security Features of Trezor Login
Trezor Login incorporates advanced, multi-layered security features that make it one of the safest authentication systems in the crypto industry.
Every login begins with a hardware-level verification process, meaning that the user must physically connect their Trezor device and confirm access. This step ensures that no unauthorized person can log in remotely.
The PIN protection system adds another critical layer. Users set up a personal PIN during initialization, and this PIN must be entered each time they log in. The on-screen PIN layout appears scrambled with each login attempt, making it impossible for spyware to guess your input.
For enhanced protection, users can enable the passphrase feature, which acts as an additional security measure beyond the recovery seed. This unique passphrase can create hidden wallets, ensuring that even if someone gains access to your recovery phrase, they cannot reach your private funds without the secret phrase.
Unlike browser-based wallets, Trezor Login also protects users from phishing attacks. It only works through official Trezor websites or the Trezor Suite app, preventing access through fake or malicious pages. Every transaction or login attempt must be verified physically on your Trezor device screen, ensuring you always know what you’re authorizing.
Trezor Login and Trezor Suite
Trezor Suite is the official application used alongside Trezor Login. It serves as a control center for your cryptocurrency portfolio, providing access to your balances, transaction history, and exchange tools.
When you log in using your Trezor device, the Suite connects securely to your wallet, allowing you to manage assets without exposing sensitive data. Every command you give — from viewing accounts to sending funds — requires confirmation directly on your Trezor hardware wallet. This process guarantees that even if your computer is compromised, no transaction can be executed without your approval.
Within Trezor Suite, users can also benefit from privacy tools such as Tor integration, which hides your IP address and enhances anonymity while managing cryptocurrencies online.
Setting Up Trezor Login for the First Time
Setting up your Trezor Login is quick and straightforward. Begin by downloading the official Trezor Suite application from the Trezor website. Connect your Trezor hardware wallet to your computer using a USB cable. The software will detect the device automatically and guide you through the setup steps.
You’ll be asked to create a PIN code to protect your device, followed by generating a recovery seed — a series of 12 or 24 words that act as a backup to restore your wallet if your device is lost or damaged. This recovery seed should always be written down and stored securely offline.
Once your device is initialized, you can enable additional features like the passphrase option for extra security. After setup, logging in becomes as easy as connecting your device, entering your PIN, and confirming access — no passwords or accounts to remember.
Privacy and Data Protection
Privacy is one of the core principles behind Trezor Login. It does not store any personal information or user data. All authentication and verification steps happen locally on your device, without relying on third-party servers.
Additionally, Trezor Suite is open-source software, meaning anyone can inspect its code to verify that it contains no hidden data tracking or security vulnerabilities. This transparency builds trust and ensures users maintain full control over their digital assets.
For users who prioritize anonymity, Trezor Suite offers Tor network support, which allows all internet communication to pass through encrypted channels. This prevents third parties from tracking your IP address or online activity while using your wallet.
The Benefits of Using Trezor Login
Trezor Login offers a combination of simplicity, transparency, and robust protection that few other systems can match. It eliminates the need for traditional passwords, which are often the weakest point in digital security. Instead, it uses physical verification that only you can control.
By keeping private keys offline and never transmitting them over the internet, Trezor ensures that your funds are safe from online attacks, keyloggers, and phishing schemes. Every action you take must be confirmed on your device, putting full control in your hands.
Moreover, the interface of Trezor Suite makes managing multiple cryptocurrencies easy, even for beginners. It combines advanced features like in-app exchanges, portfolio tracking, and privacy tools in a simple and visually clear environment.
Troubleshooting Trezor Login
If you ever face issues with Trezor Login, most problems are minor and easily fixed. Ensure that Trezor Bridge, the communication software that links your device to your computer, is properly installed and running. Check that your USB connection is stable and that you’re using the latest version of both Trezor Suite and your device’s firmware.
If your device is not detected, restarting your computer or trying a different USB port usually solves the issue. Always make sure you are logging in through the official Trezor Suite or Trezor.io website to avoid phishing risks.
Why Trezor Login Is the Safest Option
Trezor Login redefines what it means to access digital assets securely. By combining hardware-level protection, offline private key storage, and open-source transparency, it offers one of the most trusted systems in the crypto world.
While online exchanges and software wallets rely on centralized servers and password protection, Trezor puts the power back in your hands. No third party ever has access to your keys, accounts, or data. This self-custody model ensures that your funds are truly yours and cannot be frozen, hacked, or stolen through traditional means.
Conclusion
Trezor Login stands as a gold standard in crypto security. It replaces fragile password-based systems with hardware authentication that guarantees total ownership and protection. Every time you log in or authorize a transaction, your Trezor device ensures it’s really you — and that your private keys never leave your hands.
Whether you’re managing a small crypto portfolio or significant digital investments, Trezor Login offers the safety, privacy, and simplicity needed to secure your assets in a world full of digital threats.
Disclaimer
The content provided here is for educational and informational purposes only. It should not be interpreted as financial, investment, or trading advice. Cryptocurrency investments are inherently risky and volatile. Always conduct independent research or consult with a financial advisor before making investment decisions.